Remediating vulnerabilities in BMC Helix Automation Console

The benefits include:
- Ability to remediate vulnerabilities even if TrueSight Server Automation is restricted on cloud devices due to corporate policy.
- Ability to remediate vulnerabilities even if TrueSight Server Automation does not have the remediation for newly discovered vulnerabilities.
Scenario
Workflow for remediating vulnerabilities in BMC Helix Automation Console by using Ansible Automation Platform
The following table lists the tasks that you need to perform to integrate BMC Helix Automation Console with BMC Helix Intelligent Automation and remediate vulnerabilities by using Ansible Automation Platform:
Task | Action | Product | User role | Description | Reference |
|---|---|---|---|---|---|
1. | Create the inventory in Ansible Automation Platform. | Ansible Automation Platform | Automation engineer | Add the inventory (a collection of hosts) managed by the Ansible Platform application. | |
2. | Create the credentials in Ansible Automation Platform. | Ansible Automation Platform | Automation engineer | Create the username and password required to access the Ansible Platform application. | |
3. | Create an Ansible job template to remediate vulnerabilities | Ansible Automation Platform | Automation engineer | Install the vulnerability remediation script in Ansible Automation Platform. | |
2. | Configure the Ansible Automation Platform connector | BMC Helix Intelligent Automation | Automation engineer | Configure the cloud connector to establish a connection between BMC Helix Intelligent Automation and Ansible Automation Platform (formerly called Ansible Tower). | |
5. | Integrate BMC Helix Automation Console with BMC Helix Intelligent Automation | BMC Helix Automation Console | Administrator | Enable Intelligent Automation integration from the BMC Helix Automation Console UI | |
4. | Create an automation policy | BMC Helix Intelligent Automation | Operator | Create an automation policy that will remediate vulnerabilities identified by BMC Helix Automation Console. This policy is triggered when a vulnerability remediation operation is executed in BMC Helix Automation Console. | |
6. | Create a vulnerability remediation operation | BMC Helix Automation Console | Operator | Create a vulnerability remediation operation that will trigger the automation policy when you execute it. | |
7. | View automation policy run history | BMC Helix Intelligent Automation | Automation Engineer | View the History page to view the status of the automation policy run. |
To create a policy for remediating vulnerabilities by using Ansible Automation Platform
- Click Policies and then click Create Automation Policy.
- In the Policy Information section, enter a unique name and an optional description for the policy.
- Select Automatic to execute the policy automatically based on the incoming events.
In the Trigger section, on the Paste Event JSON tab, enter the event in the JSON format, and click Done.
The Trigger Condition is generated based on the selected event. Remove the source hostname and continue with the next steps.
- Click anywhere in the Trigger Condition box to start building the expression for a trigger condition, and use the suggested parameters, values, and operators to complete the expression.
For sample expressions, see Trigger condition expression. - To add action to the policy, click Select Action and perform the following steps by using the action wizard:
- From the Pick an automation tool section, click the Ansible Automation Platform connector name.
Only configured connectors are displayed here. The wizard takes you to the next step to select an action. - Click Sync Actions.
All job template and workflow template actions in your Ansible Automation Platform instance appear. - (Optional) Use the Search Online option to dynamically search for actions in the Ansible Automation Platform application.
- Click Select against the required action.
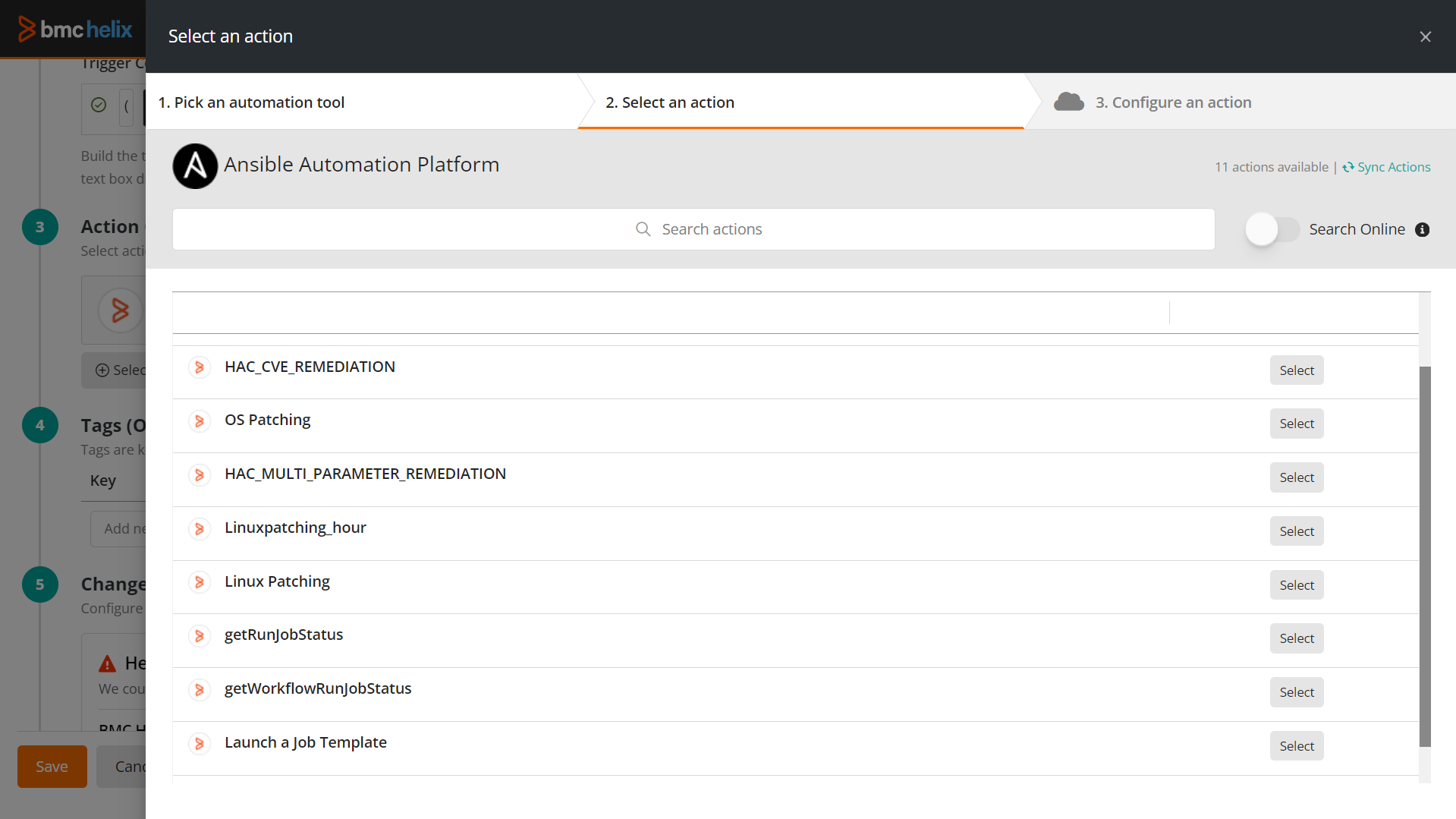
The wizard takes you to the next step to configure an action. - Provide the following information:
- Enter the action name and description.
In Request body, enter the extra variables that you might have used in Ansible Automation Platform:
Sample request body for stopping an AWS EC2 instance{
"extra_vars": {
"node": "$.event.asset_name",
"cve_list": [
"$.event.cve_ids"
]
}
}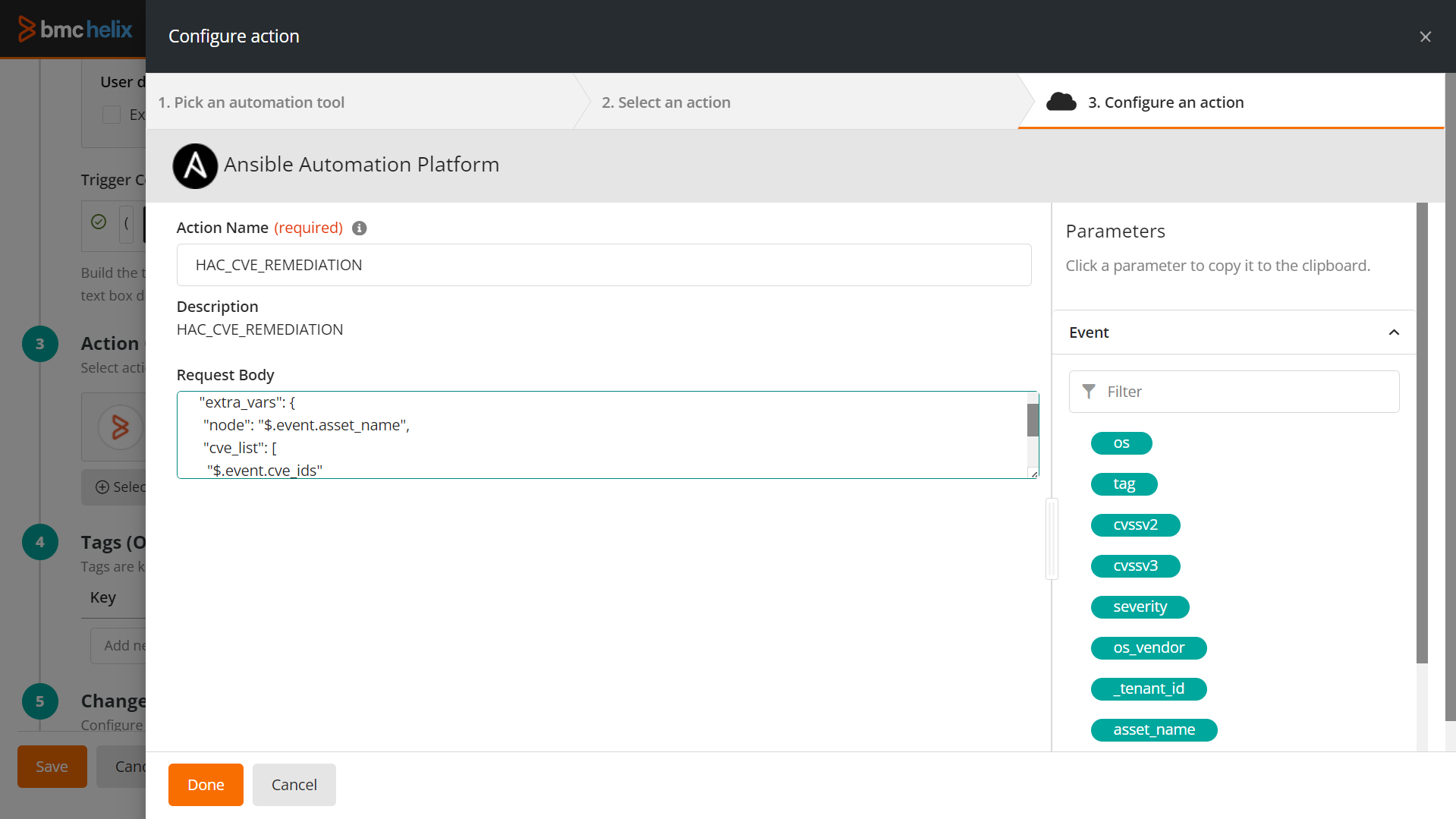
- Click Done.
The added action appears in the Action Configuration section on the Create Automation Policies page.
- From the Pick an automation tool section, click the Ansible Automation Platform connector name.
- Select Publish Policy and click Save to publish the policy.
Where to go from here
After you create the automation policy, you can create a vulnerability remediation operation in BMC Helix Automation Console. See Create a vulnerability remediation operation.
When you execute the vulnerability remediation operation, the created automation policy is triggered in BMC Helix Intelligent Automation and the selected vulnerabilities are remediated by using the Ansible automation platform. To view the status or other details of the policy run, go to the History page. For more information, see View automation policy run history.