Integrating with BMC Helix Single Sign-On
BMC Helix Single Sign-On is an authentication system that supports various authentication protocols such as LDAP and provides single sign-on for users of BMC products. For more information about BMC Helix Single Sign-On, including installation and configuration, see BMC Helix Single Sign-On Orientation.
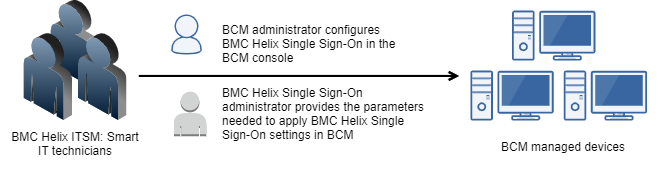
Integrating BMC Client Management with enables BMC Helix ITSM: Smart IT technicians to remote control BMC Client Management managed endpoints through the BCM browser-based console.
The BMC Helix Single Sign-On administrator typically provides the parameters needed to applyBMC Helix Single Sign-On settings in BMC Client Management. As a BMC Client Management administrator, ensure that the mandatory settings are met to ensure a successful integration.
To integrate with BMC Helix Single Sign-On, a BMC Client Management administrator must configure BMC Helix Single Sign-On parameters in the BMC Client Management console. After successfully configuring BMC Helix Single Sign-On with BMC Client Management, the BMC Helix ITSM: Smart IT administrator gets access to the BMC Client Management browser-based console to search for and remote control BMC Client Management managed devices.
Before you begin
As a BMC Client Management administrator who is integrating BMC Client Management with BMC Helix Single Sign-On, ensure that the following settings are met:
- BMC Helix Single Sign-On parameter details
- BMC Helix Single Sign-On URL
- Realm
- Certificate Authority
- Server Certificate
Mandatory settings
- The minimum supported version of BMC Helix Single Sign-On is 9.1.01 and later.
- The BMC Client Management master and the BMC Helix Single Sign-On server must be in the same domain. For example, if the BMC Client Management master server domain name is bcm.calbro.com, then the BMC Helix Single Sign-On domain name must be rsso.calbro.com.
- On the RSSO server, the realm used must have the master server DNS alias as one of the application domains. Following the above example, we must add bcm.calbro.com.
- The BMC Client Management master server must have a reservation in DNS and must be accessed using that DNS name; otherwise, the integration fails and the following message is displayed: Forbidden request! Goto URL is wrong.
- The same user must be present on both BMC Helix Single Sign-On and BMC Client Management master server; otherwise, the integration fails. For example, if AllenBrooks is authenticated through BMC Helix Single Sign-On, then a user AllenBrooks should be present on the BMC Client Management master server as well.
Considerations for configuring certificates
Communication between BMC Client Management and BMC Helix Single Sign-On can take place only over secured protocol (HTTPS). To enable communication by using HTTPS, you must obtain the HTTPS certificate from the BMC Helix Single Sign-On server.
You can supply a CA bundle that is trusted by your organization, pin the certificate downloaded from BMC Helix Single Sign-On, or use both.
A pinned certificate is more secure than a CA bundle; however, pinned certificates require more frequent renewal. BMC recommends that you use both a pinned certificate and a trusted CA bundle to verify the identity of the BMC Helix Single Sign-On server.
BMC Helix Single Sign-On parameters
As a BMC Client Management administrator, you must get the following settings from a BMC Helix Single Sign-On administrator. The following parameters are required to configure BMC Helix Single Sign-On with BMC Client Management.
| Parameter | Description |
|---|---|
| Enabled | Defines whether the BMC Helix Single Sign-On server authentication is activated. |
| RSSO Server URL | Enter the URL for the BMC Helix Single Sign-On server. The BMC Helix Single Sign-On server URL must begin with https and have the same domain as the BMC Client Management master server. For example, use bcm.calbro.com and rsso.calbro.com. |
| Realm ID | A realm is a virtual identity provider used to authenticate a domain. Contact your BMC Helix Single Sign-Onadministrator for the Realm ID. This field must not be empty. The Realm ID must exist on the BMC Helix Single Sign-On server. |
| Product Identifier | Defines the identifier for BMC Client Management. The identifier must be unique for each application that provides authentication through BMC Helix Single Sign-On server. |
| RSSO Token revalidation period | Enter the revalidation period in seconds. For more information, contact your BMC Helix Single Sign-On administrator. |
| Certificate Authority Bundle | Configures the list of certificate authorities that BMC Client Management must trust when connecting to a BMC Helix Single Sign-On server. |
| Server Certificate | Defines the server certificate to accept when connecting to the BMC Helix Single Sign-On server. This certificate is taken from the BMC Helix Single Sign-On server and it must be pinned to use the certificate. Note: You can use either the Certificate Authority Bundle or Server Certificate method. Both methods don't work together. |
You must configure a certificate on the BMC Client Management console using one of the options for security purposes.
To configure BMC Client Management to integrate with BMC Helix Single Sign-On
As a BMC Client Management administrator, you need the required parameters to configure BMC Helix Single Sign-On in BMC Client Management.
To apply the BMC Helix Single Sign-On settings, perform the following steps:
- In the BMC Client Management console, go to Global Settings > System Variables.
- In the Remedy SSO tab, enter the parameter values.
- Enable
- RSSO Server URL
- Realm ID
- Product Identifier
- RSSO Token revalidation period
- Certificate Authority Bundle
- Server Certificate
- Click OK.
Troubleshooting
| Issue | Cause(s) | Resolution(s) |
|---|---|---|
BMC Client Management integration with BMC Helix Single Sign-On not successful | Incorrect BMC Helix Single Sign-On parameters BMC Helix Single Sign-On server down | Contact BMC Helix Single Sign-On administrator |
Cannot authenticate into BMC Client Management browser-based console | BMC Helix Single Sign-On server down Incorrect BMC Helix Single Sign-On credentials Incorrect configuration in BMC Client Management | Contact BMC Helix Single Sign-On administrator to ensure BMC Helix Single Sign-On server is up and running Contact BMC Client Management administrator to check whether BMC Helix Single Sign-On is correctly configured |
Next step
Connect to the BMC Client Management browser-based console using BMC Helix Single Sign-On credentials
Comments
Log in or register to comment.