Restricting users from uploading and viewing files with specific extensions
You can restrict AR System users from uploading and viewing files with specific extensions in Mid Tier . This restriction can help prevent users from uploading malicious attachments and viewing them.
Best practice
To restrict attachments
Important
The AR System Administration: Server Information form shows the local level value of the configuration. If a local value does not exist, the form displays the global level configuration. If you modify the value on this form, the local level configuration value is modified.
For example, if a configuration shows global level value and you modify the value by using this form, the local level value gets created for the configuration.
- In a browser, open the AR System Administration Console, and click System > General > Server Information.
The AR System Administration: Server Information form appears. - Click the Attachment Security tab as shown in the following figure.
Enter the attachment options that you need, and click Apply.
The following table describes the available options.Field name Description Attachment criteria - Allow all attachments—No restrictions on uploading attachments
- Allow attachments with following extensions—Upload attachments with extensions listed in Comma separated list of limit extensions.
- Disallow attachments with following extensions—Do not upload attachments with extensions listed in Comma separated list of limit extensions. All other attachments are allowed.
Important
If you disallow attachments with specific extensions, this impacts all the features that have attachments. For example, Import Export features or email attachment. To avoid this, you can add related exception form to the Attachment exception list.
For example, For executing a UDM job if the attachment extension is disallowed, add DMT:ErrorException form in the Attachment exception list.
Comma separated list of limit extensions Attachment extensions that are allowed or not allowed, based on the Attachment criteria selected. Attachment exception list The list of Form names (field ID) for which attachment limitations do not apply—for example, Data Visualization Module (3450298).
If the user uploads any attachment in the form fields specified in attachment exception list, these fields are not validated and the attachments are uploaded without verification in the fields.
Attachment validation plugin name Name of the custom validation plug-in that you developed for verifying attachments.
The custom validation can perform any function per your requirements. You can develop the plug-in for performing functions like verifying the attachment containing malicious content, verifying whether the attachment is a virus, verifying whether the user has changed the extension for uploading the attachment, and so on.
An example custom plug-in might be named EXAMPLE.ARF.SIMPLE.
If you are using a C plug-in, add the .dll/.so path in the ar.cfg or ar.conf file in the following format to load the plug-in:
Plugin: <CompletePath>/myplugin.dllThe custom validation plug-in should be a Filter API plug-in, which has only one API. Following is the prototype for the API:
void ARFilterApiCall(void *object, ARValueList *inValues, ARValueList *outValues, ARStatusList *status)object—Name of the objectinValues—Indicates that it has only one value, which is of attachment typeoutValues—Indicates that it has only one value, which is of attachment type only when status is warning; otherwise, the value isNullstatus—Indicates the status of the attachment validation (OK,WarningorError). If the status isWarning, the outValue is used for saving attachment data.
Display criteria - Allow display of all attachments—Users can view all the attached files by clicking the Display button in the Attachments pool.
- Allow display of attachments with the following extensions—Users can view attached files that have extensions specified in Comma separated list of display extensions.
- Disallow display of attachments with the following extensions—Users cannot view attached files that have extensions specified in Comma separated list of display extensions. All other attachments are allowed.
- Disallow display of all attachments—Users cannot view any attachment.
The display criteria are applied to all the existing extensions in the Mid Tier application.
Comma separated list of display extensions Lists the attachment extensions that you want to allow or not, based on Display criteria.
Attachments flowchart
The following flowchart helps you understand the attachment security based on the options that you select from the Attachment criteria list.
Attachment security flowchart
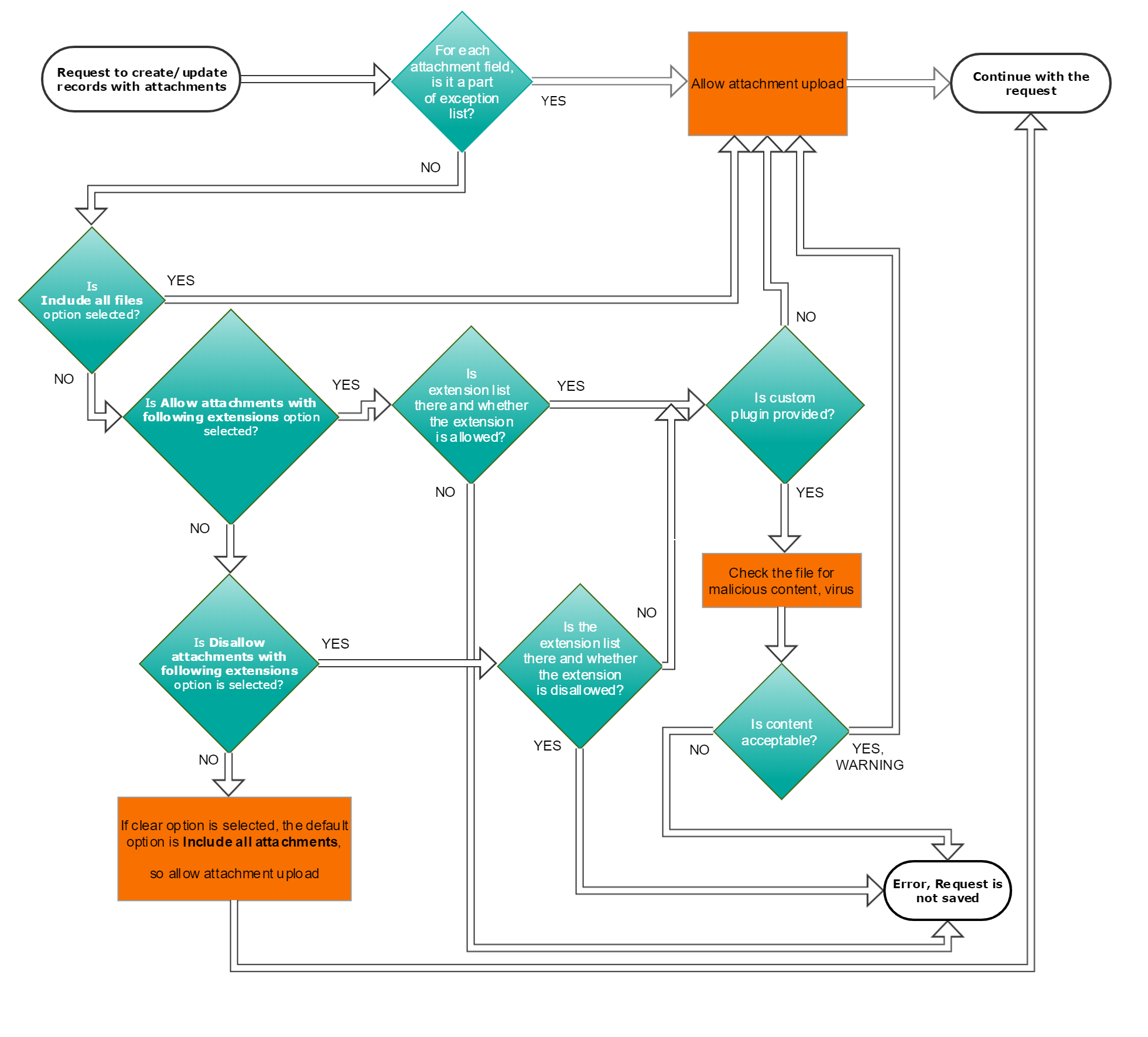
Scenarios for restricting attachments
The following table lists examples of parameter values for requests that include attachments:
| Parameter | Scenario 1 | Scenario 2 | Scenario 3 | Scenario 4 | Scenario 5 | Scenario 6 |
|---|---|---|---|---|---|---|
| Attachment criteria | Allow all attachments | Allow attachment with the following extensions | Allow attachment with the following extensions | Allow attachments with the following extensions | Disallow attachments with the following extensions | Disallow attachments with the following extensions |
| Comma-separated list of limit extensions | doc xls jpg gif | doc xls jpg gif | doc xls jpg gif | doc xls jpg gif | exe dll db | exe dll db |
| Attachment exception list | - | Data Visualization Module(41006), Report (2000012) | - | - | - | - |
| Attached File examples | example.dll, example.gif | example.jar (JAR File field on Data Visualization Module form) | example.doc, example.jpg | example.exe, example.db | example.doc, example.txt | example.exe, example.dll |
| Status | File is attached. All attachment options are permitted. | File is attached. The JAR File field ID is added to the attachment exception list. | File is attached. Its extension is on the list of permitted extensions. | File is not attached. Its extension is not on the list of permitted extensions. | File is attached. Its extension is not on the list of disallowed extensions. | File is not attached. Its extension is on the list of disallowed extensions. |
To disable users from viewing the content of specific types of files
- In a browser, open the AR System Administration Console, and click System > General > Server Information.
The AR System Administration: Server Information form appears. - Click the Attachment Security tab, shown in the following figure.
- Enter the display options that you need, and click Apply.
For any particular attachment that you want to view, the Display button in Remedy Mid Tier or the Display menu command in the Remedy User Tool is enabled only if Display criteria enables you to view that attachment. For all other attachments, the Display button or menu command is dimmed

Comments
Log in or register to comment.