Reauthentication
Some BMC applications are designed to provide an additional security level to some business critical functionality available to end users. This protection mechanism invokes a reauthentication request, and end users are asked to provide their credentials when they perform some action in the system, for example, approving a service request.
Remedy Single Sign-On handles authentication requests from applications integrated with them differently. Depending on how a realm is configured, Remedy Single Sign-On processes authentication requests in one of the following ways:
- Enables automatic reauthentication—end users are not required to provide the user name and password at the time of reauthentication on the Remedy Single Sign-On login page.
- Enables manual reauthentication—end users are required to provide their credentials at the time of a reauthentication request.
Automatic reauthentication
End users are automatically authenticated at the time of a reauthentication request, only if a single authentication method is configured for a realm, and if this method is one of the following:
- Kerberos
- Certificate-based
- Preauthentication
- SAML—when configured not to display the login page for end users.
Manual reauthentication for a realm with a single authentication method
If you have one of the following authentication methods configured for a realm, the reauthentication is manual, and end users are required to provide their credentials on the login page at the time of the reauthentication request:
- AR
- LDAP
- Local
- OpenID Connect
- SAML configured to display the login page for end users
For SAML and OpenID Connect IdPs, the login page of the IdP is displayed at the time of the reauthentication request.
For AR, Local and LPAD IdPs, the Remedy Single Sign-On login page is displayed.
Manual reauthentication for a realm with a chain of authentication methods
If you have an authentication chain configured for a realm, you can enable manual reauthentication. The secondary authentication in the chain is invoked at the time of a reauthentication request, and end users are required to provide their credentials on the login page at the time of the reauthentication request.
The following diagram shows how reauthentication works for a realm with several authentication methods:
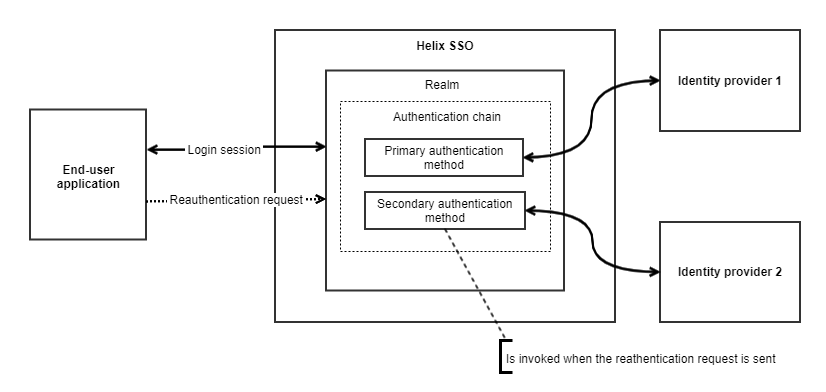
To configure manual reauthentication for a realm with several authentication methods, chain them in accordance with the principles described in the following table:
| Authentication type | Authentication methods supported | Notes |
|---|---|---|
| Primary authentication |
| SAML note: If SAML IdP is configured not to display the login page to end users, then you must enable the Bypass for reauth requests setting in SAML configuration of the realm. For information about this setting, see Importing configuration from an identity provider and configuring SAML. Preauthentication notes:
|
| Secondary authentication |
| For OpenID Connect IdPs, the login page of the IdP is displayed at the time of the reauthentication request. |
Comments
Log in or register to comment.