Setting up LDAP or Active Directory users in Remedy SSO
You can configure the Remedy Single Sign-On server to authenticate TrueSight Presentation Server users through an LDAP server.
The following topics help you to perform the LDAP/AD configuration tasks in Remedy SSO and create an authorization profile in the TrueSight console:
Before you begin
- You must have installed and configured the Remedy SSO to work with the Presentation Server and its component products. For details, see
Planning to deploy Remedy SSO
and Installing Remedy Single Sign-On.
- You must migrate the internal user data from Atrium SSO to Remedy SSO. For details, see
Migrating internal user data from Atrium SSO to Remedy SSO.
- You must have set the Remedy SSO general settings. For details, see
Set up the Remedy SSO server.
- You must have configured tenants to be used with the Presentation Server. For details, see Configuring tenants for the Presentation Server in Remedy SSO.
Configuring LDAP or Active Directory users in Remedy SSO
To configure local authentication for use with App Visibility Manager
Add local authentication if your system includes integration with App Visibility Manager, Synthetic Monitor, or both.
- Log in to the Remedy SSO console as an Admin user.
- Click the Realm tab.
- Select a tenant (realm) with LDAP authentication.
In the left navigation pane of the Edit Realm page, click Authentication.
- Click Enable Chaining Mode.
- By the List of Authentications, click Add Authentication.
- From the Authentication Type list, select LOCAL.
- Click Save to save the authentication type, and click Save to save the chain of authentication.
To create or edit an authorization profile with LDAP users in the Presentation Server
- Log in to the TrueSight console as a Super Admin.
- Navigate to Administration>Authorization Profiles.
- Create a new authorization profile or edit an existing authorization profile to associate the user groups from Active Directory.
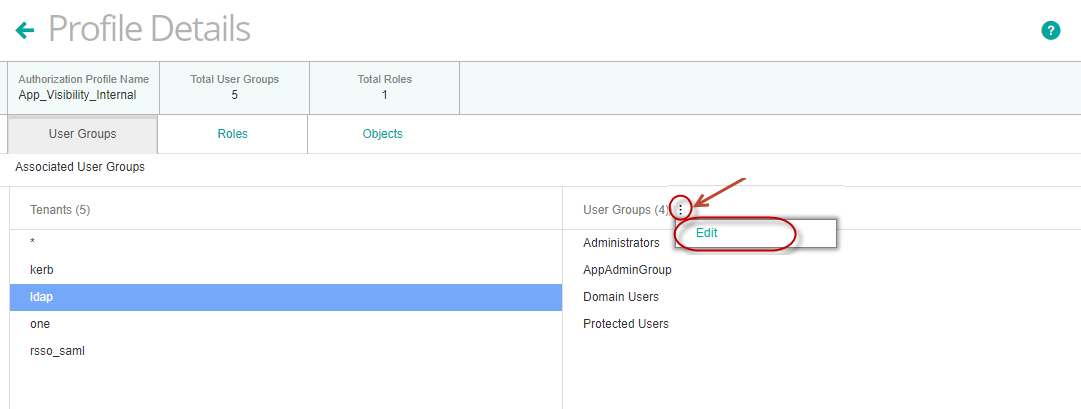
- Select the tenant that you configured in Remedy Single Sign-On for Active Directory users and select Edit under User Groups.
- Click Add and select the Active Directory user group from the list of user groups.
- Select the required roles from the list roles.
- (Optional) Select the required objects from the list of object.
- Select OK and then Save.
- Select Yes to confirm changes to the authorization profile.
- Log out of the TrueSight console.
- Log in to the TrueSight console as an Active Directory user.
- Log in to the Infrastructure Management server as an Administrator and perform the following steps:
- Edit the self_collector.mrl file located at /pw/server/etc/<cellname>/kb/collectors/ and add the groups to the permissions that are needed.
r - Read-only
w - Write
x - Execute
- Save the self_collector.mrl file.
- Recompile the cell using the commands
mccomp -n <cellname>mcontrol -n <cell> restart
- Edit the self_collector.mrl file located at /pw/server/etc/<cellname>/kb/collectors/ and add the groups to the permissions that are needed.
Was this page helpful? Yes No
Submitting...
Thank you
Comments
Is there a more refined way to do step 12...? Kind of strange that all the other changes are done in the console but I have to modify a config file manually on the server for this one step. Not everyone has access to the server - a little bit restricting.
Hi Ali Khoshkar,
Editing an MRL file is supposed to be restricted and therefore, only an Admin user can do that task.
Some use cases might fail if that step is not performed.
Log in or register to comment.